Understanding And Mitigating 10 Common Internet Appsec Threats
A web utility is software that runs on an internet server and is accessible through web application security best practices the Internet. Many internet functions are business important and contain sensitive customer data, making them a useful target for attackers and a high precedence for any cyber safety program. What follows is the OWASP Top Ten listing of internet application safety risks, up to date most just lately in 2021.
What’s Utility Security – How Does It Work & Best Practices
TDR options use signatures to detect known threats and behavior-based detection to detect unknown rising Prompt Engineering threats. Some TDR solutions can detect highly evasive malware, zero-day assaults, and advanced persistent threats (APTs) that always evade conventional defenses. Development teams use SCA to efficiently track and analyze all open-source parts pulled right into a project.
Software Security Testing Vs Api Safety Testing
Regularly evaluation and replace user entry permissions to ensure that solely authorized people have the required privileges. Learn about this security risk assessment service your organization can use (with blue groups and purple teams) to proactively establish and remediate IT safety gaps and weaknesses. The application safety process entails a series of important steps geared toward figuring out, mitigating and stopping safety vulnerabilities. Learn extra about Snyk’s holistic method to software safety posture management, a greater method for modern organizations to handle software risk. Application risk administration helps a company shield itself in opposition to attacks, enhance productivity, guarantee enterprise continuity, ensure regulatory compliance, and strengthen belief with companions and clients.

Step 6: Inspect And Track Vulnerabilities
This helps software program keep strong and safe from vulnerabilities that modifications or updates would possibly introduce. For occasion, an administrator may need entry to all functionalities of an software, whereas a guest user may have limited visibility. Discover its importance, various types, testing strategies and software tools to make sure sturdy app protection. By mitigating the varied techniques that attackers can use to compromise purposes, software security helps forestall such risks. For that cause, managing application safety is amongst the most important pillars of any cybersecurity technique.
Application Safety Greatest Practices
Static application safety testing (SAST) is a technique of analyzing source code for safety vulnerabilities at an early stage of development. It examines code with out executing it, figuring out safety points corresponding to SQL injection, XSS, and buffer overflows. SAST instruments present reviews, highlighting code sections and vulnerabilities, permitting builders to remediate points effectively. Application security (AppSec) includes safeguarding applications in opposition to threats throughout their lifecycle.
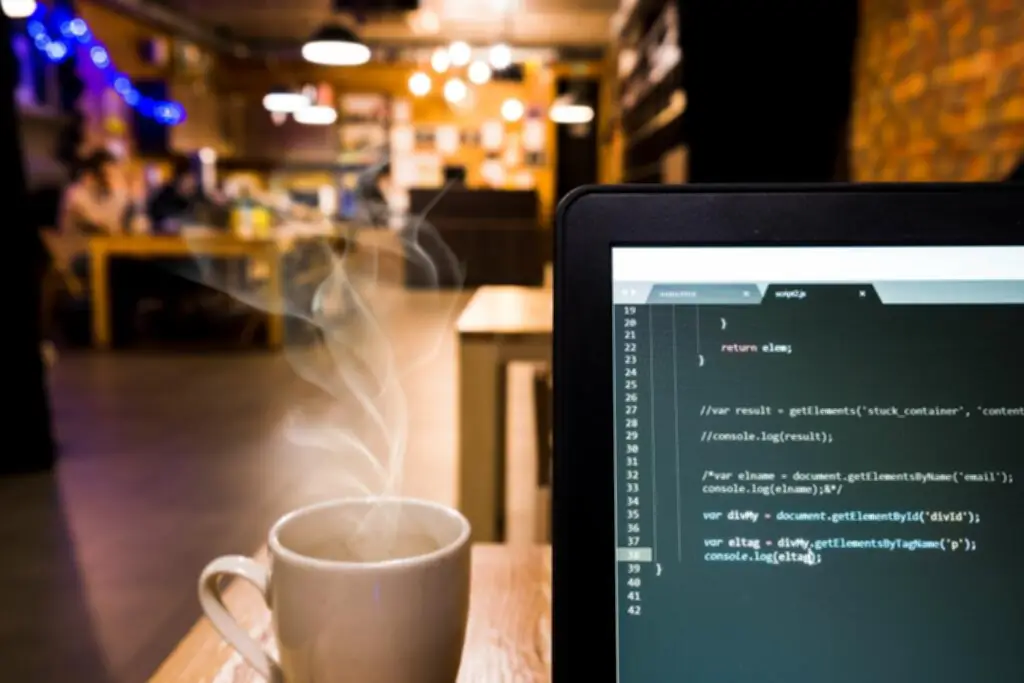
This complete information from SaltyCloud explains the significance of application safety danger administration (ASRM), exploring the crucial roles of context, knowledge, accountability, and privateness regulations. However, the most common software safety threats based on the OWASP Top 10 are broken access control, cryptographic failures, and injection (including SQL injection and cross-site scripting). By using the latest tools for safety scanning and monitoring, as nicely as the most recent secure coding practices, builders and their organizations can restrict their exposure. By following these software security risk assessment steps, organizations can decrease threat and adjust to relevant regulatory requirements. Prioritizing utility safety testing is necessary to construct functions that folks belief and rely on.
Threats which might be addressed by traditional cybersecurity programs also apply to SAP methods. The challenge facing most organizations operating SAP is knowing which patches are needed and applying them consistently. This is a painstaking process that leaves large numbers of SAP systems unpatched for long durations of time.
- From endpoint administration to native safety, IBM MaaS360 provides an end-to-end UEM solution.
- This encompasses mobile apps on our smartphones, internet functions in our browsers, on-premise functions, and cloud functions working on distant servers.
- It is important to set sensible safety expectations and repeatedly monitor and replace your safety protocols to remain ahead of evolving threats.
- It prevents attackers from gaining insights into the appliance’s construction or potential vulnerabilities based on error outputs.
- The cell utility landscape is dynamic, with new technologies and threats emerging frequently.
Another necessary aspect of cloud native safety is automated scanning of all artifacts, in any respect stages of the development lifecycle. Most importantly, organizations must scan container photographs at all levels of the event course of. The most extreme and common vulnerabilities are documented by the Open Web Application Security Project (OWASP), within the form of the OWASP Top 10. Of course, application security exists inside the context of OSes, networks and other related infrastructure parts that must also be secured.
Interactive Application Security Testing (IAST) combines elements of SAST and DAST, providing real-time analysis of functions from within. IAST instruments are deployed inside the utility runtime surroundings, monitoring its behavior and identifying vulnerabilities as they happen throughout normal utilization and testing processes. SQL injection (SQLi) happens when an attacker manipulates a SQL query by way of the input knowledge from the consumer to the applying. This can lead to unauthorized access to delicate info, deletion of data, or full takeover of the database.

Occurring after the invention of a “zero-day vulnerability,” an exploit is a targeted assault towards a system, community, or software program. This assault takes benefit of an missed security downside, looking to cause unusual behavior, harm data, and steal data. Ensure you handle privileges carefully and cling to the principle of least privilege. Implementing overly advanced security procedures or too many instruments can lead to your security practices being ignored in the long run. Being conscious of those threats equips you to higher safeguard your cloud sources and knowledge. Mistakes like making information publicly accessible or not using correct encryption may give hackers easy access.
This is the method by which an organization may determine potential security threats and decide how probably these threats could probably be exploited by cybercriminals. Because of this, application security risk administration is a vital part of the method that ensures the safety of applications and protects organizations from varied safety threats. By implementing efficient utility risk administration strategies, businesses and organizations can safeguard their very important property and keep their customers’ and stakeholders’ belief and loyalty. Utilizing established safety frameworks and tips like NIST and OWASP is crucial for companies to adequately manage various software security dangers. With a NIST application safety framework, organizations can readily establish and tackle potential security risks.
Application security, or appsec, is the practice of using safety software, hardware, methods, finest practices and procedures to protect computer applications from exterior safety threats. Industry assets such as OWASP present guidance and pattern methodologies for creating threat rankings. Tools like Snyk AppRisk present tools to manage and automate the chance scoring process inside the context of a complete threat administration program. Organizations should identify which compliance and regulatory requirements they have to adhere to based mostly on location, business, and different relevant factors related to the application and where/how it functions. It’s important to incorporate all regulatory and compliance wants inside the structure of a danger management framework. Security measures ought to present a good return on funding – you must implement these measures that may provide the most effective protection contemplating your price range and different constraints.
These two plans are key to driving the group towards its development in the market. The ASRM offers an accurate evaluation of risk for individual applications, every category of functions and the organization as a whole. Organizations can use this method to limit entry to a cluster or server, permitting only licensed and needed connections. Once a monitoring course of detects suspicious exercise, organizations utilizing microsegmentation can isolate the affected methods to stop threats from spreading throughout the SAP environment. Integrating SAP safety monitoring right into a centralized SIEM could be complicated but is very useful.
Transform Your Business With AI Software Development Solutions https://www.globalcloudteam.com/ — be successful, be the first!














.jpeg)
.jpeg)
.jpeg)
.jpg)









